I find this quite a disturbing read! Detaining/arresting small children?! Disturbing especially when one looks at the military training drills that have been going on here in NZ since as far back as 2015, drills to ‘quell civil unrest’. Drills within and involving communities.
Continue reading ICE Admits To Databasing Americans And Creating Social Credit Scores – ‘We Have A Nice Little Database And Now You’re Considered A Domestic Terrorist’Tag Archives: cybersecurity
There are over 11,000 data centres worldwide; where are they and why do they want them?
from Visual Capitalist
via expose-news.com
Visual Capitalist has mapped where in the world the approximately 11,000 to 12,000+ operational data centres are located. What do they need all these data centres for?
“Data centres are the backbone of the digital economy, storing, managing and processing the world’s data. In this graphic, we visualise the countries with the most data centres as of November 2025, revealing where the world’s digital infrastructure is concentrated,” Visual Capitalist said and produced the image below.
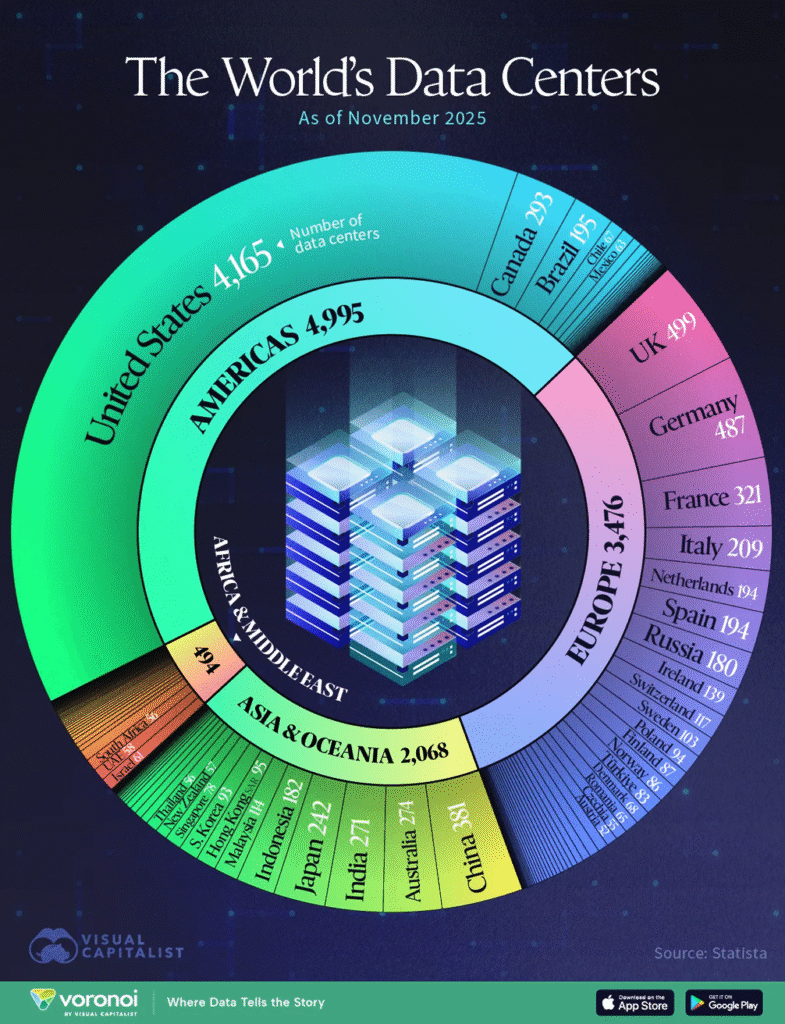
What do they plan to use all these data centres for? The following recently published articles give us some idea. To read the full article, follow the hyperlink in the subtitle.
We’re Making Utter Fools Of Ourselves While Claiming To Have Reached The Apex Of Wisdom
Society seems to be rushing headlong toward replacing God and humans with “giant statistical prediction machines” in a trend that seems as inevitable as it is concerning. Last week, an Axios report heralded the rise of “chatbot Jesus” and AI pastors. The day following that report a video advertising a service to turn deceased loved ones into eternal virtual companions went viral.
These ominous news bits come on the heels of Sam Altman’s announcement that ChatGPT would now offer erotica to its adult customers (and Elon Musk’s xAI already offered similar degenerate features). But as much as society is bent on its rushing, there’s an age-old warning that should cause humanity to pause: We become like what we worship.
Paul McCartney to Release Silent AI Protest Song After UK Relaxes Copyright Protections for Tech Firms
Legendary Beatles singer Paul McCartney will be releasing a silent music track next month in protest of the United Kingdom relaxing copyright protections for tech firms to push generative AI.
Artists have alleged that a recent change in copyright law “would make it easier to train AI models on copyrighted work without a license”.
“Under the heavily criticised proposals, UK copyright law would be upended to benefit global tech giants. AI companies would be free to use an artist’s work to train their AI models without permission or remuneration,” the artists said, adding that changes “would require artists to proactively ‘opt-out’ from the theft of their work – reversing the very principle of copyright law.”
Twitch Imposes Face Scans for UK Users to Comply with Government’s Censorship Law
British Twitch users are waking up to a new form of surveillance disguised as “safety.” The platform, owned by Amazon, has begun enforcing a requirement that forces viewers to undergo facial recognition scans before accessing mature-rated streams in the United Kingdom.
The change, made to satisfy the UK’s controversial Online Safety Act, effectively links biometric identification to entertainment and sets a precedent that privacy advocates have long warned could normalise state-aligned digital tracking.
Launching a High Court Challenge Against Australia’s Social Media ID Check Law
A High Court showdown looms as Australians question whether privacy and free speech can survive the nation’s new digital gatekeepers.
The Online Safety Amendment (Social Media Minimum Age) Bill 2024, scheduled to take effect on December 10, 2025, will require all users to prove they are over 16 before accessing major platforms such as Facebook, Instagram, TikTok, YouTube, X, and Snapchat. To comply with this, people will have to give up their privacy by verifying with a government-issued ID.
Australia’s online digital ID checks and under-16 social media ban are now facing a constitutional challenge, with a coalition of Australians led by NSW Libertarian MP John Ruddick preparing to contest the new law in the High Court.
EU’s Weakened “Chat Control” Bill Still Poses Major Privacy and Surveillance Risks, Academics Warn
The European Union stands poised to vote on one of the most consequential surveillance proposals in its digital history.
The legislation, framed as a measure to protect children online, has drawn fierce criticism from a bloc of senior European academics who argue that the proposal, even in its revised form, walks a perilous line. It invites mass surveillance under a veil of voluntarism and does so with little evidence that it will improve safety.
Life Under Digital ID: A Global Analysis with Solutions
Above Phone has produced a report that answers the following questions about digital ID programmes:
- How are they being rolled out?
- Where will they be mandatory?
- What will life be like with digital ID?
- How much time do we have?
- What can we do about it?
To access a copy of the report, you will need to sign up for Above Phone’s emails by providing a name and email address.
Last week, Hakeem Anwar, founder of Above Phone and Take Back Our Tech, joined Derrick Broze to discuss his new deep dive into the latest developments on digital IDs from around the world. Anwar outlines where digital IDs are advancing the fastest, where they are yet to roll out, and what you need to know to be prepared. You can watch this interview on Voluntary Tube, Substack (transcript available), BitChute or Odysee.
Taiwan Warns of Security Risks and Political Bias in Chinese AI Models
Taiwan’s NSB identified alarming cybersecurity vulnerabilities in five Chinese AI models, including unauthorised data harvesting, location tracking and forced privacy policy acceptance.
These AI models can generate malicious scripts and exploit vulnerabilities, posing risks of remote cyberattacks, and systematically push CCP narratives.
Lawsuit Claims Google Secretly Used Gemini AI to Scan Private Gmail and Chat Data
When Google flipped a digital switch in October 2025, few users noticed anything unusual. Yet, according to a new class action lawsuit, something significant had changed beneath the surface.
Plaintiffs claim that Google silently activated its artificial intelligence system, Gemini, across its communication platforms, turning private conversations into raw material for machine analysis.
The lawsuit accuses Google of enabling Gemini to “access and exploit the entire recorded history of its users’ private communications, including literally every email and attachment sent and received.”
And More …
Biometric Update provides some further reasons why they require so many data centres :
- Suprema teases plan for new AI-powered access control solution at partner event: ‘Automation will define the future of AI in security’ says Suprema Founder
- Zurich Airport rolls out EES biometric border control with secunet
- IATA: Replace physical airport barriers with biometric digital ID to save costs
- Amadeus’ on-the-move airport biometrics corridor roll out at scale in Indonesia
- German govt signs EUDI Wallet collaboration agreement with over 75 companies
- Mattr leads work on digital credential issuance platform for NZ govt agencies
- Law enforcement warned of ‘existential’ threat from ubiquitous technical surveillance
- ICE’s license plate app quietly expands a nationwide surveillance web
- Major AI, DPI initiatives to support Africa single digital market unveiled
- Mandatory identity verification for UK companies goes live
- Shipping association presents new identity exchange for secure KYC
Featured image: Server Racks With Plexus Lines And Connection Dots In The Warehouse. Source: Getty Images

Header photo credit: pixabay.com
Ending your right to free speech – ‘digital ID required’ by 2027 for you to access the internet
From nationaldefensemagazine.org
via technocracynews.com
TN has examined this topic in detail several times. Ultimately, the only people who will be able to hop on the Internet, regardless of the entry point (5G, 6G, fiber optic, private of public WiFi) will first have to be definitively identified. This will require a personal, registered ID comparable to an electronic passport. No digital ID? You don’t use the Internet. Got ID? Every activity is tracked, catalogued and saved. The military is paving the way for this. ⁃ TN Editor
The Defense Department has finally laid out its plan for protecting its cyber networks after years of pledging to make it a commitment.
The Office of the Chief Information Officer released “The DoD Zero Trust Strategy” in November — which laid out metrics and deadlines for the department to achieve full zero trust adoption by 2027. Cybersecurity experts said the government and private sector should work together to leverage resources to successfully enter the new regime.
“Cyber physical threats to critical infrastructure really are one of our biggest national security challenges that we’re facing today, and that the landscape that we’re dealing with has gotten more complex,” Nitin Natarajan, deputy director at the Cybersecurity and Infrastructure Security Agency, said during a MeriTalk event in October.
Cyber attackers have more resources than they have in the past, and it’s less expensive to do a lot of damage to an unsecure system, he said. It’s not just lone wolf hackers, but nation states and cyber terrorists who can pose a threat.
For example, the 2019 SolarWinds cyber attack, which swept past the defenses of thousands of organizations, including the federal government, has been linked to Russia-backed operatives.
The new strategy’s basic tenet is that treating organizations’ security like a moat around a castle doesn’t keep out bad actors.
“Mission and system owners, as well as operators, increasingly embrace this view as fact. They also see the journey to [zero trust] as an opportunity to affect positively the mission by addressing technology modernizations, refining security processes and improving operational performance,” the document said.
Zero trust culture requires every person within a network to assume that it is already compromised and requires all users to prove their identities at all times.
The strategy lists technologies that can help cultivate a zero trust environment such as continuous multi-factor authentication, micro-segmentation, advanced encryption, endpoint security, analytics and robust auditing.
While these various technologies can be used to implement this basic premise, it essentially means that “users are granted access to only the data they need and when needed.”
The strategy revolves around four pillars: accepting the culture of zero trust, operationalizing zero trust practices, accelerating zero trust technology and department-wide integration. The strategy notes that while IT departments across the Pentagon may need to purchase products, there is no one capability that can solve all their problems.
“While the objectives prescribe ‘what’ shall be done in furtherance of the goal, they do not prescribe ‘how,’ as DoD Components may need to undertake objectives in differing ways,” the strategy read.
For the technology pillar, the Pentagon’s zero trust strategy calls for capabilities to be pushed out faster while reducing silos. Capabilities that promote simpler architecture and efficient data management are also important, according to the document.
While many methods can be used to authenticate users, the integration pillar calls for creating an acquisition plan for technologies that can be scaled department-wide by early fiscal year 2023.
One technology development already underway is the Thunderdome, a $6.8 million contract awarded to Booz Allen Hamilton earlier this year. The technology would protect access to the Secure Internet Protocol Router Network, the Pentagon’s classified information transmitter, according to a Defense Information Systems Agency press release.
It won’t be possible to completely retrofit every legacy platform with technology such as multi-factor authentication, the strategy points out. However, the services can implement safeguards for these less modern systems in the interim.
The securing information systems pillar will also require automating artificial intelligence operations and securing communications at all levels.
Automating systems is an important part of zero trust, said Andy Stewart, senior federal strategist at digital communications company Cisco Systems and a former director at Fleet Cyber Command/U.S. Tenth Fleet. If the processes behind zero trust don’t work well, people can struggle to use the technology and adopt the zero trust mindset.
“Zero trust is about raising the security, but it also means, ‘How do I operate more efficiently?’” he said. “The user experience should get a vote.”
While the strategy marks a turning point for the effort, the Pentagon started down the road of zero trust years ago. Its 2019 Digital Modernization Strategy mentioned that zero trust was an emerging initiative concept it was “exploring.”
Accepting more rigorous cybersecurity measures through the zero trust mindset is something the Marine Corps has been working on through education and raising awareness, said Renata Spinks, assistant director and deputy chief information officer of information, command, control, communications and computers and acting senior information security officer.
“We spend a lot of time educating, because if people know what they’re doing and why they’re doing it … it has been my experience that they will get on board a whole lot sooner than resisting,” she said
The 2021 zero trust mandate from President Joe Biden’s administration was “a godsend” because it gave justification for personnel inside the Marine Corps who may not have understood the necessity of some of the IT initiatives, she said.
A successful zero trust implementation will reduce threats to some of the most critical types of capabilities that warfighters will be relying on in the future: cloud, artificial intelligence and command, control, communications, computer and intelligence.
The military needs the help of defense contractors to protect sensitive data, Spinks noted. Industry can help the military’s IT personnel understand how to work with the type of data that they will be providing and to how much the military will need access.
“Zero trust will not be zero trust successfully if we don’t get help in managing identities,” she said.
The Marine Corps recently hired a service data officer who could use input from contractors about how much access the military will need to figure out the best ways to classify and manage the service’s data, she noted.
Having access to secure data anywhere will help military members and personnel in the defense industrial base who are working outside of business hours and in remote locations, according to the Pentagon’s strategy.
The push for zero trust is different from some cybersecurity initiatives because it has muscle behind it, Spinks added. Leadership has provided policies and procedures and are willing to be held accountable, she said.
“Cybersecurity is not an inexpensive venture. But I think what truly drives it is the vicious adversary and all of the activity across not just the federal government, but even at the state and local levels,” she said.
Better cybersecurity practices will also be needed to secure supply chains, Natarajan noted. Making them more resilient, especially in critical technologies such as semiconductors, has been a focus at the Pentagon in recent years.
“We know that this is being used by malicious cyber actors really to exploit a lot of third party risk after going after an organization’s supply chain,” he said.
That’s another reason why the government can’t work alone, he added.
“As we look at this, we’re looking at this not just from a sector perspective but also looking at this from national critical functions,” he said.
CISA released cybersecurity performance goals for companies to measure themselves in October. Though the performance goals don’t cite zero trust specifically, the goals are intended for companies to use regardless of their size.
“We’re really looking at these to be that minimum baseline of cyber protections that will reduce the rest of critical infrastructure operators,” he said. “But at the end of the day, by doing that we’re also impacting national security and the health and safety of Americans throughout the nation.”
The private sector in turn needs the government’s investment in education and resources to build up its cyber workforce.
“Cyberspace involves not just the hardware and software, the technology, your tablets, your iPhones, your technology, but it involves people. People developed cyberspace. People use cyberspace. We are in cyberspace,” Kemba Walden, principal deputy director of the National Cyber Director’s Office, said during the MeriTalk event.
Not yet at full operating capacity, the National Cyber Director’s Office was established in 2021 to take the lead on cyber issues at the federal level, including the first national cybersecurity strategy.
Just as important as the broad strategy will be the national workforce and education document that will be released after the cybersecurity strategy, Walden said.
“We took a look and recognized that 700,000 or so U.S. jobs with the word cyber in it are left unfilled,” she said. That number comes from market research firm Lightcast’s 2022 report based on 2021 data.
“As a national cyber and national security lawyer, that frightens me,” she said. “That is a national security risk from my perspective.”
In recent years, organizations such as Joint Cyber Defense Collaborative and the National Security Association’s Cybersecurity Collaboration Center have sprung up to gauge the needs and collect feedback from large enterprises, she said.
“Those are the types of collaborative efforts that I think are necessary in order to evolve public-private collaboration and information sharing overall,” she said.
Ultimately, the benefits of zero trust trickle down to the warfighter, according to the document.
For example, the Pentagon’s joint all-domain command and control effort — which aims to link sensors and shooters while using artificial intelligence to make decisions — relies on that data being secure. If it falls into the wrong hands, military leaders can’t achieve information dominance, the strategy notes.
“We need to make certain that when malicious actors attempt to breach our zero trust defenses; they can no longer roam freely through our networks and threaten our ability to deliver maximum support to the warfighter,” Chief Information Officer John Sherman said in the strategy.
SOURCE
After “Event 201” Coronavirus Simulation in 2019, World Economic Forum Now Plans “Cyber Pandemic” Simulation for July 2021
More in store from the psychopaths
By Johnny bVedmore and Whitney Webb
UnlimitedHangout.com
On Wednesday, the World Economic Forum (WEF), along with Russia’s Sberbank and its cybersecurity subsidiary BI.ZONE announced that a new global cyberattack simulation would take place this coming July to instruct participants in “developing secure ecosystems” by simulating a supply-chain cyberattack similar to the recent SolarWinds hack that would “assess the cyber resilience” of the exercise’s participants.
On the newly updated event website, the simulation, called Cyber Polygon 2021, ominously warns that, given the digitalization trends largely spurred by the COVID-19 crisis, “a single vulnerable link is enough to bring down the entire system, just like the domino effect,” adding that “a secure approach to digital development today will determine the future of humanity for decades to come.”
The exercise comes several months after the WEF, the “international organization for public-private cooperation” that counts the world’s richest elite among its members, formally announced its movement for a Great Reset, which would involve the coordinated transition to a Fourth Industrial Revolution global economy in which human workers become increasingly irrelevant.
This revolution, including its biggest proponent, WEF founder Klaus Schwab, has previously presented a major problem for WEF members and member organizations in terms of what will happen to the masses of people left unemployed by the increasing automation and digitalization in the workplace.
READ MORE





You must be logged in to post a comment.